Abbreviations and acronyms
- CCMP = combines CBC-MAC (Cipher Block Chaining Message Authentication Code) technique for constructing a message authentication code from a block cipher with Counter Mode of encryption
- GCMP combines the Galois Mode of authentication with Counter Mode of encryption.
- TK (Temporal key) is used to accomplish all encryption processes. Both WPA2, and WPA3 Personal use AES with a 128-bit key. WPA3 Enterprise uses 192-bit session key. TK can be:
- PTK - pairwise transient key for unicast
- GTK - group temporal key for multicast
- PN (Packet Number) - 48-bit is much like a TKIP sequence number (protects from replay and injection attacks). The PN shall never repeat for a series of encrypted MPDUs using the same temporal key.
- ADD (Additional authentication data) is Constructed from portions of the MPDU header, this information is used for data integrity of portions of the MAC header.
- All of the MAC addresses
- FC – MPDU Frame Control field: (green)- protected; (yellow) – set to 0; (blue) – set to 1
- Sequence Control Field:
- 4 bits fragment number is not modified
- 12 bits sequence number is masked to 0
- QoS Control field
- QC TID is used
- remaining QC fields are set to 0
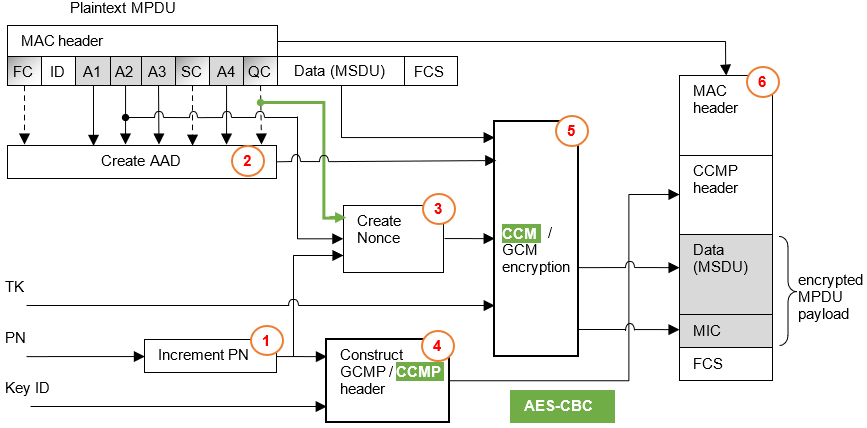
Encryption / data integrity process
CCMP/GCMP encryption & data integrity processes are looking similar:
1. Increment the PN, to obtain a fresh PN for each MPDU
2. Create AAD
3. Create Nonce
2. Create AAD
3. Create Nonce
- CCM nonce block: 13 Octets (Nonce = QoS + A2 + PN):
- 1 Octet: Priority field
- = 0, in case no QoS Control field in MPDU
- = (bits 0 to 3 = TID) + (bits 4 to 7 = 0)
- 6 Octets = MPDU address A2 field
- 6 Octets = Packet Number (PN)
- GCM nonce block: - 12 Octets: (Nonce = A2 + PN)
- 6 Octets = MPDU address A2 field
- 6 Octets = Packet Number (PN)
- the Key ID
- the Packet Number (PN)
- to create an 8-byte MIC.
- to encrypt the MSDU payload of the frame body and the MIC
6 Creating the final MPDU, which consists of:
- the original MAC header
- the CCMP / GCMP header,
- the encrypted MSDU,
- the encrypted MIC, and
- a frame check sequence (FCS) is calculated over all of the fields of the header and entire frame body. The resulting 32-bit CRC is then placed in the FCS field.
CCMP / GCMP MPDU Format
The frame body consists of:
- the CCMP / GCMP header (is not encrypted), - 8 bytes (compared to the 4 octets in WEP header)
- the Key ID and
- the packet number (PN), which is divided into 6 octets
- the MSDU upper-layer payload (encrypted)
- the MIC (encrypted) - 8 bytes
- Note that CCMP / GCMP does not use the WEP ICV
In other words, CCMP / GCMP encryption adds 16 bytes of overhead to an 802.11 MPDU.
Advantages of AES-GCM cipher
- AES-GCM is a more secure.
- The AES-GCM does not use the XOR operation for each block with the previous block as it do the AES-CBC. As a result GCM is not susceptible to counter attacks like the bit flipping.
- Message authentication (via GMAC/GHASH) is done on the ciphertext (in CBC-MAC on the plaintext)
- AES-GCM is faster.
- Instead 2 x AES operations per block in AES-CBC, it uses 1 x AES operation and 1 x GHASH per block (GHASH generally faster than AES, so GCM is faster)
- each
- Each block with AES-GCM can be encrypted independently
Links
1. Understanding
CTR with CBC-MAC Protocol (CCMP) AES-CCMP in depth – Praneeth's Blog
(praneethwifi.in)
2. Wi-Fi
Security Evolution - How we ended up in WPA3? (grandmetric.com)
3. CWSP – CCMP
Encryption Method | mrn-cciew (mrncciew.com)


No comments:
Post a Comment