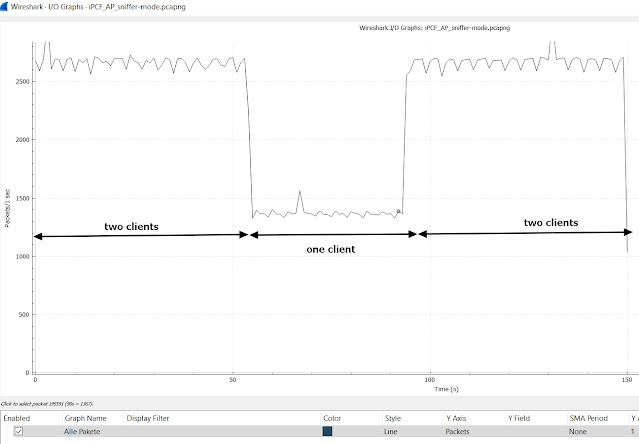
This blog post will explain basic working
principle and operation modes of the Siemens iPCF and compared to 802.11 PCF
medium access technologies. The next post will take a detailed look at the iPCF
frame format.
Before we go deeper into the Siemens iPCF
Wi-Fi, let’s review what we know about the PCF technology.
PCF
The PCF is short for Point Coordination Function. It is the medium access control (MAC) technology for a deterministic Wi-Fi communication. Two well-known Wi-Fi coordination techniques are DCF (Distributed coordination function) and EDCA (Enhanced Multimedia Distributed Control Access). Both this medium access technologies are based on CSMA/CA (Carrier-sense multiple access with collision avoidance) access method to coordinate the access to the RF-medium. In other words, all Wi-Fi devices are making the “transmit or not transmit” decision based on CSMA/CA rules. It is very important to understand that the main idea of the distributed coordination – there is no decision-making device. All participants are equal. The downside of this model is that it impossible to predict who will be the next.
Unlike DCF and EDCA, in a PCF access point coordinates the communication within the Basic Service Set (BSS). Like in the TDM (Time-division multiplexing), every client device has a time slot in the communication cycle. It means that every Wi-Fi client, connected to the AP in the PCF mode get a predicted chance to communicate with the AP.
The PCF has higher priority over the common DCF/EDCA Wi-Fi because the PIFS (Point coordination function interframe spacing) duration is shorter as than DIFS or AIFS.

Fig.1 interframe spacing
The Access Point announces in the Beacon two intervals: one for Contention Free (or PCF) and another one for Contention Based (or DCF) communication. The CF intervals begins right after the beacon and ends after the CF-End frame. During the CF time, no station is allowed to transmit without getting CF-Pool frame. The AP sends the CF-Poll frame to the PCF capable station to permit it to transmit a frame.
Fig2. PCF cycle
The PCF is less efficient compared to DCF, but the PCF has other advantages. This technology is more suitable for low data rate, low latency, low Jitter communication.
Comparison of PCF and DCF Wi-Fi:
Despite its advantages, PCF was newer implemented in the real world.
- Wait! What about the iPCF from Siemens?
- No. Honestly, the iPCF has nothing to do with PCF except time slots. Well, let’s go deeper into the iPCF from Siemens.
iPCF
iPCF is the proprietary Wi-Fi protocol from Siemens for real time deterministic wireless communication. The typical use case of the iPCF is not WLAN, but WSN (Wireless Sensor Network). The iPCF is very good compatible with the industrial Ethernet-based protocol PROFINET IO for communication between PLC and I/O stations. The main difference between the Siemens iPCF and classical WSN based on IEEE 802.15.4 Standard is the bandwidth. The 802.15.4 based communication uses 2 or 5 MHz channels and has the throughput up to 250 kbps (PHY). The iPCF has 19 Mbps (PHY). Besides this, the iPCF use channels in the 5 GHz frequency band. The 802.15.4 is designed for Sub-1GHz and 2.4 GHz frequencies. Thus, in some cases, iPCF can be more useful and more stable than the WSN based on 802.15.4, especially if clients have no power limitation.
iPCF medium access
In opposite to the PCF, the iPCF does not support the Contention Based communication.
When an iPCF client joins an iPCF access point, it is given a time slot in the iPCF cycle. It is up to AP in which order the client will be served.
There are two cycle types: the fixed cycle time and the flexible (not fixed) cycle time.
iPCF with fixed cycle time
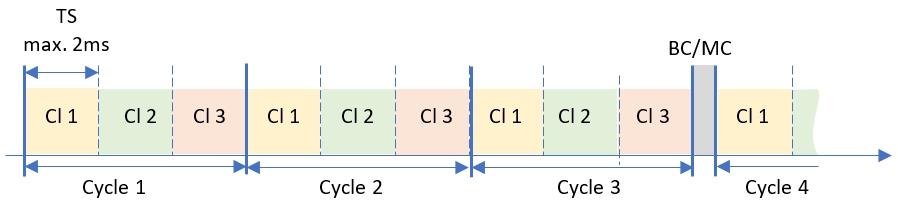
The duration of the fixed cycle time can be 8, 16, 32, 64, or 128ms. Every client get about 2ms time slot. It means that no more than 4 clients can be connected to the iPCF with the fixed cycle 8ms, no more than 8 clients per 16ms cycle, and so on. If less clients are connected as the cycle time allows, than some clients get additional time slot per cycle. The figure illustrates how the 8ms cycle looks like if three clients are connected. Note that there is a slot in the middle of the cycle, which is reserved for Broadcast and Multicast traffic.
Fig3. iPCF fixed cycle
The iPCF with fixed cycle has more practical application because the compatibility with the PROFINET protocol.
The iPCF cycle cannot be more than the PROFINET cycle.
iPCF with flexible cycle time
The iPCF with the flexible cycle time works different. The duration of the cycle is theoretically unlimited (I did not check it) and is equal the sum of time slots for all clients connected to the AP. In our example it is equal to 6ms. If a new Client joins the Access Point, the duration of the cycle is 2ms more.
Fig4. iPCF flexible cycle
There is the time slot 1ms for broadcast and multicast after every third cycle.
NOTE: In my lab I have tested only one client with one Access Point. It would be interesting to test the iPCF in case at last two Access Points use the same channel.
Conclusions & Suggestions
PCF vs iPCF
- PCF and DCF can co-exist. iPCF cannot operate simultaneously with DCF.
- the PCF cycle is divided into two intervals: contention based and contention free. The iPCF support only contention free communication.
- The iPCF is proprietary Siemens protocol.
Suggestions
- Avoid busy channels. Remember, the iPCF is not compatible with standard Wi-Fi!
- I would avoid U-NII-1 channels from 36 to 48 for following reason:
- The channel 36 is the default channel for most Wi-Fi vendors. The 80 MHz channel width is very oft the default value. The likelihood that someone will put their mobile phone into hotspot mode and the channel will be 36@80 is very high.
- In case a standard Wi-Fi access point measures a radar signal it must change the channel. Some vendors use the channel 36 as the default
- Never, never, never use 2,4 GHz channels for iPCF!
- Do not use DFS channels (U-NII-2C band).
- Siemens does not have a RRM feature. Use static channel design.
- I would recommend using of U-NII-3 channels. In most cases this band is free. Remember about EIRP limitations for this band. It is 14dBm only
References