Netsh, or network shell, is very powerful network utility that allows you to display or modify the network configuration of a computer that is currently running.Netsh, among many other things, also allows you edit wireless settings (for example, SSID), start/stop WLAN, change the key or manage WLAN profiles. To be honesst all these topics are out of scope of this post. The key point of this blog post is the Troubleshooting of the Wi-Fi communication. In this post I will show you how you can use the Netsh to localize a Wi-Fi issue from the Windows client’s side. By WLAN Troubleshooting it is sometimes important to look at the WLAN issue from the client’s perspective. Using the Netsh you can collect information about link quality, generate a WLAN report with detailed information about all last issues or even capture 802.11 frames.
Contents- Netsh SHOW Commands
- Collecting Wi-Fi link information
- netsh wlan show interfaces
- netsh wlan show wlanreport
- Checking Wireless Adapter Capabilities
- netsh wlan show wirelesscapabilities
- netsh wlan show drivers
- Netsh TRACE Commands
- Using Netsh for packet capture
- Useful Netsh Trace Filters
- Links
- Netsh SHOW Commands
- Collecting Wi-Fi link information
- netsh wlan show interfaces
- netsh wlan show wlanreport
- Checking Wireless Adapter Capabilities
- netsh wlan show wirelesscapabilities
- netsh wlan show drivers
- Netsh TRACE Commands
- Using Netsh for packet capture
- Useful Netsh Trace Filters
- Links
Netsh SHOW Commands
Collecting Wi-Fi link information
netsh wlan show interfaces
Use this command to see specific wireless adapter information, such as radio type, channel number, RSSI, up- and down-link data rate and type of authentication your computer is currently using.
PS C:\Users\itunakin> netsh wlan show interfaces There is 1 interface on the system: Name : WLAN Description : Intel(R) Wireless-N 7260 GUID : d4bced40-c85a-4912-a361-04734932bade Physical address : d8:fc:93:36:30:17 State : connected SSID : GoGo BSSID : 44:4e:6d:90:71:be Network type : Infrastructure Radio type : 802.11n Authentication : WPA2-Personal Cipher : CCMP Connection mode : Profile Channel : 13 Receive rate (Mbps) : 144.4 Transmit rate (Mbps) : 144.4 Signal : 99% Profile : GoGo Hosted network status : Not available |
“Rate” and “Signal” are most important for troubleshooting.
A signal quality between 80 and 100 percent corresponds to, the reliable connection. A signal above 70 percent is still good. Anything below 60 percent means you have a weak signal and this connection is not recommended for time sensitive communication. To calculate the received signal strength in dBm, you can use the formula: (% number / 2) - 100 = dBm. However, this is not accurate for all adapters.
Using the information about received and transmit rates, you can find out which MCS are used for downlink and uplink and, as a result, find out the information about modulation, coding rate, number of spatial streams, channel width, and guard interval. (You can use the MCS table for 802.11ac from the WirelessLAN Professionals’ site found here.) The MCS is sometimes very useful to know. For example, if the signal strength is 90% or more, and the device uses low MCS, it could mean that the receiver is affected by interference. As a result, the transmitter needs downgrade the modulation
To continually monitor and log the output of the 'netsh wlan show interfaces'
command I would kindly recommend you look at two scripts from two experienced WLAN
engineers:
- The first one is the win-wlan-data-script made by Nigel Bowden: The script uses the output of the 'netsh wlan show interfaces' and turn it into the csv format.
- The second one is from Peter MacKenzie: The Windows WLAN Monitor Script – MackenzieWiFi
- A Windows GUI to continually monitor the output from the ‘netsh wlan show interface’ command
- Configurable signal strength and data rate thresholds allow the users to control the levels at which the current signal strength and data rates will be disabled in green or red text.
- An optional log – When logging is enabled, the output from each instance of the ‘netsh wlan show interface’ command will be written to a comma separated csv file in ASCII format so it can be easily opened by tools such as Excel.
- A roaming log showing each roam.
netsh wlan show wlanreport
It's a very detailed report that can help you troubleshoot many Wi-Fi
connectivity issues.
To get the report you must run this command from a command prompt with administrator privilege.
This command generates a report showing recent wireless session information (by default from the last three days)
The WLAN reports contain a graph with details of the connectivity status, including information, such as when the connection started, when it got disconnected, errors, and more.
The graph is interactive. You can point on an icon of a invent to see a description in the summary window or just click on it to see more detailed information.
These events are color coded and can help you to diagnose problems. The
summary chart has a definition for each of the different colors.
The report also summarizes network adapters information configured on
your system, session success/failures, disconnect reasons, and a lot more. It
contains outputs for commands ipconfig /all and netsh wlan show all, among
other things.
There is also very helpful summery section which describe disconnect reason.
Options
The duration of the report can be changed. For example, to create the
report for last week use the command: netsh wlan show wlanreport
duration="7"
You can provide the path to an .etl file to use as the source of events instead of the machines event log: netsh wlan show wlanreport log="path\file.etl"
For more details see the article from Microsoft “Analyze the wirelessnetwork report”
Checking Wireless Adapter Capabilities
netsh wlan show wirelesscapabilities
More information: Miscellaneous technical details and validation
netsh wlan show drivers
Use this command to view WLAN interface and driver information such as:
- detailed information about your driver, like driver version, file name, version, date
- supported Wi-Fi standards
- security methods provided by adapters
- supported radio PHY
More information: How to manage wireless networks using Command Prompt inWindows 10
Netsh TRACE Commands
Using Netsh for packet capture
- Enable tracing for all components produces a lot of log files for processes that are not related to wireless authentication and can consume system resources.
- To start the network trace on the Wi-Fi adapter just run the command line (CMD or PowerShell) netsh trace start capture=yes scenario=WLAN traceFile= path\file.etl
- Tracing will stop when the "netsh trace stop" command is issued or when the system reboots. This command takes some time to run. Do not surprise if it takes some minutes to run.
- one of them with the extension ETL is a packet capture trace file and
- another one with the extension CAB is an archive which contains system Information, technical detail of the wireless adapter, the driver, settings, IP configuration and more.
- use Microsoft Message Analyzer and export the file to a CAP file. The problem is it does not work for decrypted packets.
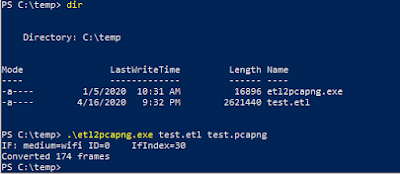
- use etl2pcapng script (the link is below). It easy to use and you do not need to install any software. Just put the ETL file and the etl2pcapng script in one folder and run the tool with: etl2pcapng.exe in.etl out.pcapng
Useful Netsh Trace Filters
|
Netsh trace
Capture Filter |
Wireshark Capture
Filter |
|
PacketTruncateBytes=<value> |
frame slice value |
|
Ethernet.Address=<xx-xx-xx-xx-xx-xx> |
wlan.addr==<xx:xx:xx:xx:xx:> |